How does this work?
Key Generation
The user provides a 64-bit key to the algorithm. This key is never used directly, instead the algorithm uses sub keys. These sub keys are generated by breaking the full key into 8 8-bit numbers. Each time the main key is used to generate a sub key the master key is rotated to the left. Due to how the rest of the algorithm works, there are exactly 192 sub keys produced and the master key rotates 3 full times and returns to its initial state. This is important for supporting the decryption algorithm. The algorithm can be modified to support 192 bits and still maintain this property.
Permutation and Substitution
Most ciphers or secret systems use some form of permutation or substitution. The ceaser cipher users substituion, substituting individual letters with others. The Rail Fence cipher is an example of a permutation cipher, no letter is changed, simply rearranged. Both of these ciphers can be attacked with frequency analysis and other analysis methods. For example ceaser cipher can be attacked by matching the first few most frequent letters in the encrypted message with the most frequent letters in the language it is written with. For english messages, the most frequent replaced with e, the next most frequent replaced with a and so on.
Both permutation and substituiton are used in this encryption algorithm. The difference that makes this algorithm more resistant to this is that substituion and permutation are used in combination, creating a permutation substitution network. The benefit of doing this is that the final product has resilance to most analysis methods, making the ciphertext more secure.
This algorithm borrows the substituion table used in the Skipjack algorithm developed by the NSA, which was classifed in 1998 and NIST not longer recomended its use after 2010 for unrelated reasons. This table takes in 8-bit number and replaces it with another 8 bit number.
The permutation system used by the algorithm is borrowed from the twofish algorithm developed by Bruce Schneier, John Kelsey, Doug Whiting, David Wagner, and Chris Hall. The permutation takes advantage of applying the XOR logic gate to mutiple sub keys.
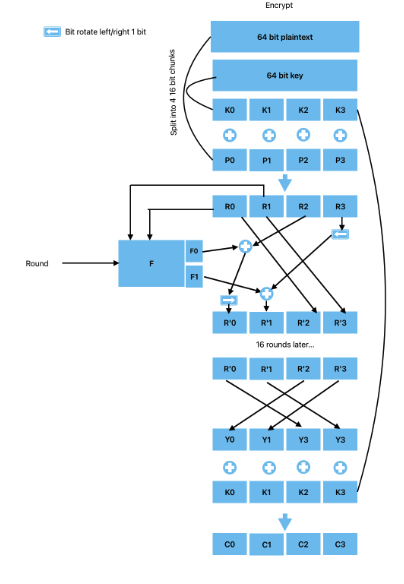
Fiestel structure
Like many common encryption algorithms such as DES and AES, this encryption system takes advantage of the Fiestel structure.Fiestel structurs are a system in which only half of the message is encrypted in each round. After each round the half of the message that was just encrypted gets swapped so the side that was untouched this round will be affected next round. This is done for 16 rounds to increase resistance to analysis attacks. The image to the left shows the full encryption process. The fiestel structure is applied near the end of each round when R0 and R1 become R'2 and R'3 and R2 and R3 go through permutatuin and substituiton before becoming R'0 and R'1.
Decryption
One of the great benefits of this algorithm is that the encryption and decryption work exactly the same. The only difference is the key generation. When decrypting the keys are generated in reverse. This is a result of the fiestel structure. This mirrors other algorithms like DES that only have an encrypt algorithm and no decrypt algorithm